There isn’t one rule that fits all organisations for privacy risk management; it comes down to the contexts, needs and priorities of the organisations itself. In a recent webinar I attended, it was stated that risk management generally leads to one of three outcomes:
- Accept - Organisations can accept risk on the basis that the process under consideration is worth potential consequences.
- Transfer - Organisations can transfer risk by outsourcing to a third party or vendor to protect the area of concern.
- Mitigate -Organisations can mitigate the risk by scoping and leading the implementation of IT security changes, controls and initiatives.
Regardless of accepting, transferring or mitigating risk, you don’t need to be an information privacy expert to understand the correlation between an organisation’s privacy practice and its preparedness to respond to a data security incident. It’s quite clear; poor privacy structures and processes significantly decrease an organisation’s ability to respond with efficiency, effectiveness, and completeness. To validate this statement, in its recent research report, Osana found organisation’s with poor privacy practices were 80% more apt to experience a data security incident compared to organisations shown to have stronger practice.
Although it’s commonly stated “it’s not a matter of if, but when” in relation to dealing with a data security incident, organisations continue to struggle with implementing data privacy protocols according to a recent TechRepublic study.
If an organisation chooses to mitigate its risk, of the three options this is usually the more difficult to manage because of potential impacts on time, budgets and personnel within the organisation to facilitate mitigation strategies. Even so, when it’s all said and done, how does an organisation know its risk mitigation practices, programs and processes actually work?
To assist with insights on this, RTG has designed a process that analyses qualitative data to calculate an organisation’s Preparedness to Respond (“PtR”) score. This process uses 104 data points which are ‘best practice’ towards information security risk management. The PtR score includes elements of technology controls, IT processes and systems, policy and compliance, stakeholder knowledge and training, and team/support structures. Each element has its own rating in terms of its risk impact (low versus high impact), and influence on an organisation’s response preparedness (low versus high preparedness).
As an example, formal processes such as a Data Breach Response Plan can positively influence an organisation’s preparedness to respond to a data security incident. However, if stakeholder training or communication is not effective, this will negatively influence an organisations preparedness.
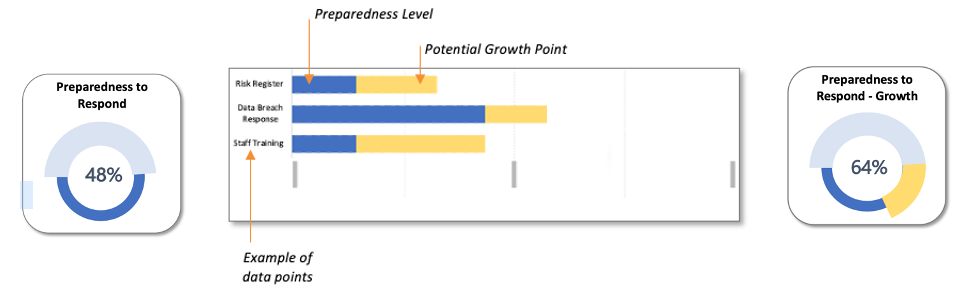
RTG has facilitated this PtR process in a number of organisations from within education and local government sectors and the outcomes have generated deep insight into the respective approaches towards risk management and what opportunities exist to minimise risk.
So, how can an organisation strengthen its privacy practice? Better still, how can an organisation gain insight on whether its risk mitigation practices, programs and processes actually work? The PtR scoring system is one way to find out. A mentor once told me “you can’t manage what you can’t measure”. It’s through the use of PtR metrics where you can identify, and measure, what elements are having the highest impact on risk mitigation proactivity, and where to focus attention to strengthen a safe, secure digital network. All based on your organisation’s contexts, needs and priorities.
If you’re interested to learn more about RTG’s Preparedness to Respond process, please reach out to me to discuss.
(p) 1300 362 456
















