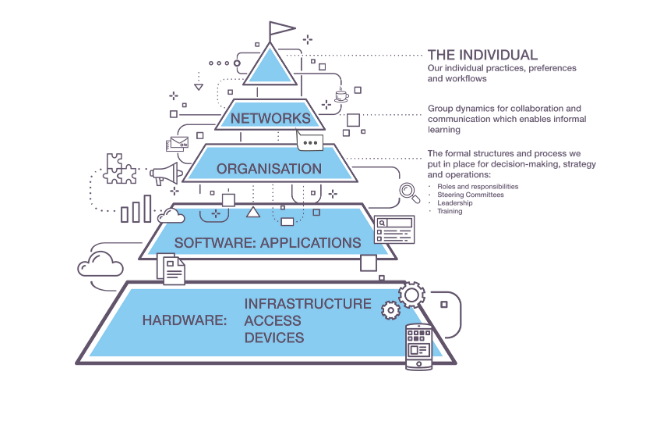
Even before COVID, an organisation’s obligation to safeguard its data had never been greater. Not only do you have to collect, store, process and discard data in ways that are compliant with regulations, you also need to have strong information security policies and practices to protect your data from malicious or unauthorised use.
The protection on an organisation’s digital assets can best be defined as a “numbers game”. The defenders of data assets must be right 100% of the time. However, the attackers only have to be right one time. Expertise in the protection of data assets is defined by mastering the basics of information security.
Some examples of these basics include, but aren’t limited to, patch management, multi factor authentication, access and permission controls, backups, content filtering and monitoring, and so on.
However, the most challenging area to master for an organisation adopting and implementing data security controls, are its people.
We can all agree the protection of data assets is challenging enough due to the agile nature in which it flows in an organisation’s network. This complexity stems mostly by the people operating and using data assets, and not by the digital systems and security controls attempting to secure them. An organisation may have the most up-to-date and progressive policy in place to manage, protect and control data assets, and as described above, fit the category of being a solid defender 100% of the time. However, it’s the people in the organisation having low adherence with policy and their respective roles and responsibilities towards data security that causes risk vulnerability to the organisation’s digital network and data ecosystem.
To assist an organisation with insight on their risk of data assets throughout the information lifecycle, RTG has created an approach to assess current workflows and structures relating to data handling management. The Data Lifecycle & Management Review (“DLM”) ascertains the intent and effectiveness of organisational policy and process.
The DLM is based on a framework built around three domains that gathers input from stakeholders at multiple points, providing a clear picture of the strengths and gaps in the organisation’s data handling and records management practice:
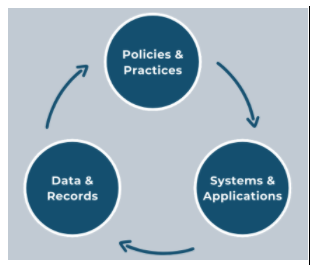
- Policies and Practices: guidelines that outline expectations on what practices to adopt across each stage of the information lifecycle.
- Systems and Applications: the systems and applications used to operationalise data assets and records.
- Data & Records: either digital or paper-based, assets that are created to facilitate business-as-usual operations and objectives.
Through this framework, RTG collects data from within your organisations that tells us how uses create data and then where it journeys from there and what they do at the end.
All organisations have preferred locations where data is created, whether that be a core system or in O365 or Google but once that data is created and saved its journey becomes less clear. Who is it shared with, is it copied elsewhere, is it converted to hard copy and what happens with that data moved outside that core system?
The chart below is an example of a typical data workflows RTG’s collected from a large independent school reviewed earlier this year. Whilst it’s a complex, yet pretty looking visualisation, in this chart example, we are looking at the volume of data or records shared via a particular application.
There is a lot to unpack in this data and the other collected, but one example of what it revealed was is in the far-right column that I have circled. The questions here in the very large-sized green box, when asked how records are deleted or destroyed, staff’s common practice is “I do not delete from my device”.
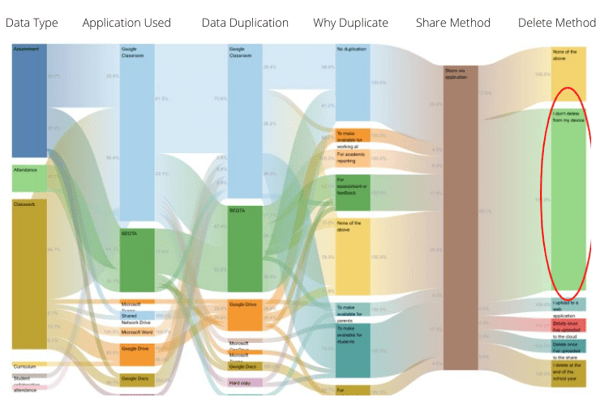
This practice significantly increases data risk vulnerability due to the potential of duplicated records and significant increase the risk of a violation of several privacy regulations that could potentially result in a financial and reputational risk to the school should an investigation take place by regulating bodies.
Numerous requirements and regulations against data handling is a complex affair for organisations to ensure appropriate risk mitigation practices are positioned against each stage of the data (information) lifecycle. Organisations have many processes and are regulated against how they create or collect data. Then there are processes and regulations on how to use that data, how to share and with whom, how and where to store data. RTG’s Data Lifecycle & Management Review (DLM) helps identify gaps in the implementation of your organisations’ data lifecycle, and how everyday practices of people are impacting the risk profile of your organisation. With a particular focus on storage, archiving, and deletion processes, the DLM uncovers recommended actions and initiatives for an organisation to strengthen its record management usage and strategy.
Organisations wanting their staff to follow a particular data handling practices, not only need to set the objectives they want to achieve, but they also need to understand whether people are following those practices and what risk not following these create. Without this view, schools are running blindly to what possible data breach or incident may be just around the corner.
If you’re interested in learning how a potentially harmful data breach can be prevented, feel free to reach out. I'll happily take you through the necessary steps to tackle any vulnerabilities that may exist that require immediate attention.
(p) 1300 362 456